























Jan 08, 2020

Tim Gasper
Chief Product Officer

Digital experiences encompass more of our lives each year from Netflix binge-watching to work tools. Unfortunately with all this utility, digital threats and misuse loom larger than ever. The billions of digital records breached or stolen in 2019 and a $19B+ third-party data industry growing at record speed compound the issue. In response, consumers are pushing back. This prompts the government to pass regulations and forces companies to secure consumers' private data.
In May 2018, the EU General Data Protection Regulation (GDPR) took effect, pushing European and global companies to collect consumer consents, respect the right to privacy, to not be tracked, and to be forgotten. Companies are also responsible for providing info on how data is being used if requested by the consumer among a variety of other key rights.
And now, as of January 1st, 2020, the California Consumer Privacy Act (CCPA) is in effect. Companies under the scope of this regulation collect personal information on California residents, have $25M or more in revenue, 50,000 or more consumer records collected, or 50% or more of revenue coming from the sale of data.
Technology - as much as people and process - plays an important role in helping companies to mitigate risks and create trust with consumers, especially as it relates to proper management and governance of data.
For example it can help answer some of the following questions:
What are consumers consenting to, and how do they revoke consent?
How do we manage privacy questions and Subject Access Requests (SARs) for copies of data and usage information?
How do I know the consumer is who they say they are?
Where does consumer personal data live?
How can I respond effectively within 45 days to a subject access request?
What are the approved consents for the data?
What is the purpose of the data usage downstream?
How do I ensure downstream analytics and usage of data conforms with consumer consents and correct purpose?
How does consumer data move and change throughout our systems?
What data is being shared and monetized with 3rd parties?
Typically a variety of different technologies must effectively work together to answer these questions. Data catalog and governance solutions are critical to this effort.
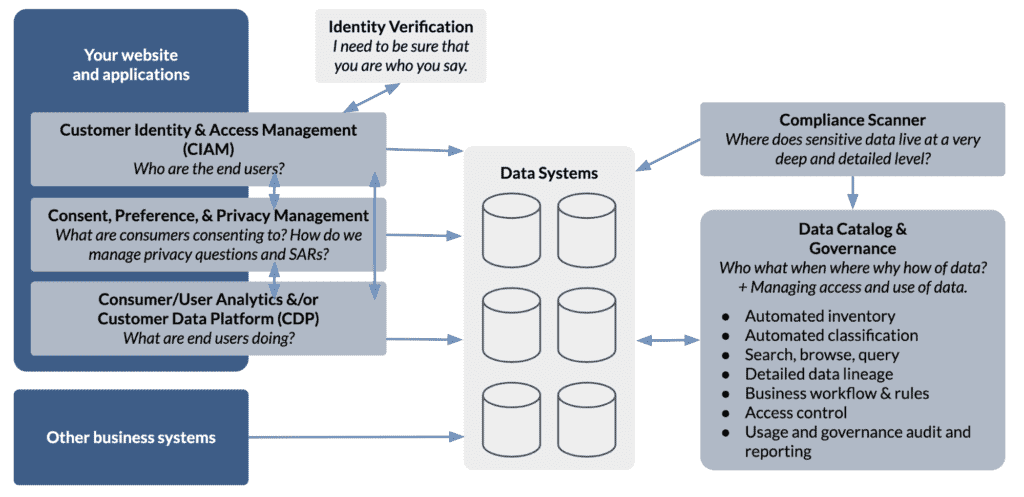
Figure 1: A CCPA-ready reference architecture with key technology examples for properly managing consents and personal information and managing downstream data usage, including data catalog and governance.
Consumer/User Analytics and Customer Data Platforms (CDP)
A very common tool in the marketing toolkit - the ability to track what users are doing on your apps and websites. Examples: Adobe Analytics, Google Analytics, or CDPs like Tealium, Segment, Heap, and Lytics.
Customer Identity and Access Management (CIAM)
Login, registration, and profile management to allow consumers to have logged-in digital experiences that remember you - for websites, apps, customer support portals, and more - and for companies to securely collect and manage personal information. Examples: Akamai Identity Cloud (formerly Janrain), SAP Customer Data Cloud (formerly Gigya), Auth0, Forgerock, Okta, Ping, and Microsoft Azure AD B2C.
Consent, Preference, and Privacy Management
Providing centralized ways of providing and revoking consents, submitting subject access requests (SARs), managing workflows around SAR response and other privacy management business processes, publish privacy policies and terms of use to digital assets, and more. Examples: OneTrust, DataGrail, and TrustArc.
Identity Verification
When an end user submits a SAR, how do you know they truly are who they say they are? Otherwise you are exposing a potentially large security hole where bad actors can try to steal information. CIAM and requiring login is one level of protection, multi-factor authentication (MFA) is another, but stronger identity verification/validation is sometimes required such as Jumio, Socure, and Experian Identity Verification provide.
Data Catalog and Governance
While the above technologies help with properly collecting consented data, managing consent, and ensuring the right people access the right information, what about downstream usage of the data for analytics purposes? How do you effectively inventory and govern the use of personal data in your complex, multi-cloud data ecosystem? That’s where services like data.world step in.
Compliance scanning
Beyond data catalog and governance solutions, even deeper scanning may be a business requirement for your company, which introspects on not just databases and data storage, but even places even such as company emails, messaging and chat services. An effective data catalog and governance solution should integrate with these solutions to provide a comprehensive, actionable view. Examples: Integris, Dataguise, and Ground Labs.
When evaluating a data catalog software for supporting your CCPA compliance strategy, consider the following key capabilities:
Automated metadata inventory - Understand what is out there, and begin to work to classify and organize it, and build semantic layers on top. You can’t manage what you can’t see, and we help you get visibility and understanding.
Automated classification / ML tagging - Leverage automated intelligence to organize and classify your information assets, including automatically identifying which ones may be sensitive in nature.
Increasing the reach of a compliance scanning solution - If you are using a compliance scanner like Integris, Dataguise, and Ground Labs, import the metadata from those tools into your catalog to increase the reach and relevance of that information. It will help enhance catalog related governance and access management as well.
Data lineage - Understand how information relates to each other, and how sensitive data may be flowing downstream, or where it came from upstream to assist with root cause analysis and remediation efforts.
Data masking and custom types - Controlling what data values are exposed, masked, or hidden as part of the catalog information.
Role-based access management and approval flows - Ensuring only the right groups and individuals have access to metadata or other information assets, and/or can take edit or administrative actions on them.
Usage and governance reporting - Understand the state of your metadata and how users are using the catalog to monitor and track safe usage as well as audit information assets, including ones classified as sensitive.

Digital experiences encompass more of our lives each year from Netflix binge-watching to work tools. Unfortunately with all this utility, digital threats and misuse loom larger than ever. The billions of digital records breached or stolen in 2019 and a $19B+ third-party data industry growing at record speed compound the issue. In response, consumers are pushing back. This prompts the government to pass regulations and forces companies to secure consumers' private data.
In May 2018, the EU General Data Protection Regulation (GDPR) took effect, pushing European and global companies to collect consumer consents, respect the right to privacy, to not be tracked, and to be forgotten. Companies are also responsible for providing info on how data is being used if requested by the consumer among a variety of other key rights.
And now, as of January 1st, 2020, the California Consumer Privacy Act (CCPA) is in effect. Companies under the scope of this regulation collect personal information on California residents, have $25M or more in revenue, 50,000 or more consumer records collected, or 50% or more of revenue coming from the sale of data.
Technology - as much as people and process - plays an important role in helping companies to mitigate risks and create trust with consumers, especially as it relates to proper management and governance of data.
For example it can help answer some of the following questions:
What are consumers consenting to, and how do they revoke consent?
How do we manage privacy questions and Subject Access Requests (SARs) for copies of data and usage information?
How do I know the consumer is who they say they are?
Where does consumer personal data live?
How can I respond effectively within 45 days to a subject access request?
What are the approved consents for the data?
What is the purpose of the data usage downstream?
How do I ensure downstream analytics and usage of data conforms with consumer consents and correct purpose?
How does consumer data move and change throughout our systems?
What data is being shared and monetized with 3rd parties?
Typically a variety of different technologies must effectively work together to answer these questions. Data catalog and governance solutions are critical to this effort.

Figure 1: A CCPA-ready reference architecture with key technology examples for properly managing consents and personal information and managing downstream data usage, including data catalog and governance.
Consumer/User Analytics and Customer Data Platforms (CDP)
A very common tool in the marketing toolkit - the ability to track what users are doing on your apps and websites. Examples: Adobe Analytics, Google Analytics, or CDPs like Tealium, Segment, Heap, and Lytics.
Customer Identity and Access Management (CIAM)
Login, registration, and profile management to allow consumers to have logged-in digital experiences that remember you - for websites, apps, customer support portals, and more - and for companies to securely collect and manage personal information. Examples: Akamai Identity Cloud (formerly Janrain), SAP Customer Data Cloud (formerly Gigya), Auth0, Forgerock, Okta, Ping, and Microsoft Azure AD B2C.
Consent, Preference, and Privacy Management
Providing centralized ways of providing and revoking consents, submitting subject access requests (SARs), managing workflows around SAR response and other privacy management business processes, publish privacy policies and terms of use to digital assets, and more. Examples: OneTrust, DataGrail, and TrustArc.
Identity Verification
When an end user submits a SAR, how do you know they truly are who they say they are? Otherwise you are exposing a potentially large security hole where bad actors can try to steal information. CIAM and requiring login is one level of protection, multi-factor authentication (MFA) is another, but stronger identity verification/validation is sometimes required such as Jumio, Socure, and Experian Identity Verification provide.
Data Catalog and Governance
While the above technologies help with properly collecting consented data, managing consent, and ensuring the right people access the right information, what about downstream usage of the data for analytics purposes? How do you effectively inventory and govern the use of personal data in your complex, multi-cloud data ecosystem? That’s where services like data.world step in.
Compliance scanning
Beyond data catalog and governance solutions, even deeper scanning may be a business requirement for your company, which introspects on not just databases and data storage, but even places even such as company emails, messaging and chat services. An effective data catalog and governance solution should integrate with these solutions to provide a comprehensive, actionable view. Examples: Integris, Dataguise, and Ground Labs.
When evaluating a data catalog software for supporting your CCPA compliance strategy, consider the following key capabilities:
Automated metadata inventory - Understand what is out there, and begin to work to classify and organize it, and build semantic layers on top. You can’t manage what you can’t see, and we help you get visibility and understanding.
Automated classification / ML tagging - Leverage automated intelligence to organize and classify your information assets, including automatically identifying which ones may be sensitive in nature.
Increasing the reach of a compliance scanning solution - If you are using a compliance scanner like Integris, Dataguise, and Ground Labs, import the metadata from those tools into your catalog to increase the reach and relevance of that information. It will help enhance catalog related governance and access management as well.
Data lineage - Understand how information relates to each other, and how sensitive data may be flowing downstream, or where it came from upstream to assist with root cause analysis and remediation efforts.
Data masking and custom types - Controlling what data values are exposed, masked, or hidden as part of the catalog information.
Role-based access management and approval flows - Ensuring only the right groups and individuals have access to metadata or other information assets, and/or can take edit or administrative actions on them.
Usage and governance reporting - Understand the state of your metadata and how users are using the catalog to monitor and track safe usage as well as audit information assets, including ones classified as sensitive.
Get the best practices, insights, upcoming events & learn about data.world products.